Background
As of June 24th, an ongoing supply chain attack is targeting the WordPress.org plugin repository. The attacker is releasing infected versions of random WordPress plugins, compromising the security of numerous websites and applications that use those plugins.
The issue has been first reported by WordFence threat intelligence in an article.
While it’s impossible to know the scale of the attack, multiple cases have been recorded shown in Figure 1.
| Plugin | Version | Date | Status |
| SEO Optimized Images | 2.1.2 | 2024-06-28 | Patched by WP.org |
| PowerPress Podcasting plugin by Blubrry | 11.9.4 | 2024-06-28 | Patched by WP.org |
| Ad Invalid Click Protector (AICP) | 1.2.9 | 2024-06-28 | Patched by WP.org |
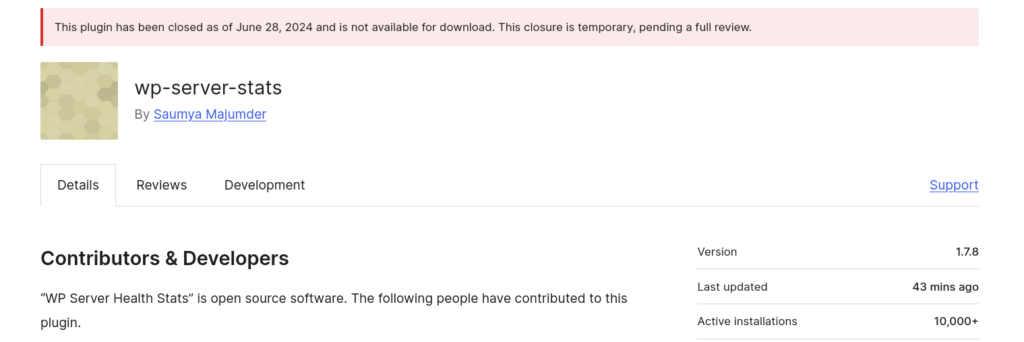
| WP Server Health Stats | 1.7.6 | 2024-06-28 | Patched by WP.org |
| Social Warfare | 4.4.6.4 – 4.4.7.1 | 2024-06-24 | Patched by Author |
| Blaze Widget | 2.2.5 – 2.5.2 | 2024-06-24 | Patched by WP.org |
| Wrapper Link Element | 1.0.2 – 1.0.3 | 2024-06-24 | Patched by WP.org |
| Contact Form 7 Multi-Step Addon | 1.0.4 – 1.0.5 | 2024-06-24 | Patched by WP.org |
| Simply Show Hooks | 1.2.1 | 2024-06-24 | Patched by WP.org |
The malicious code injected into the source code of the affected plugins performs several harmful actions:
1. Creation of administrator accounts
The code creates unauthorized admin accounts and sends the login details to a remote source, such as the IP address 94.156.79.8.
2. Injection of malicious code in your theme
It also injects malicious code into the WordPress theme’s functions.php file.
Attack Origins
The origin of the supply chain attack is currently unclear. It may be stemming from compromised WordPress.org developer accounts or an internal security incident, hopefully we will get more details soon.
Attack Response
As a crucial first step, the WordPress Plugin Directory Team temporarily closed the infected plugins to prevent further spread of malicious code.
Next, they proceed with removing the injected malicious code from affected plugins. They are also adding an admin notice to inform users about the issue and the steps taken to address it. This ensures users are aware of the incident and can take any necessary actions to protect their sites.
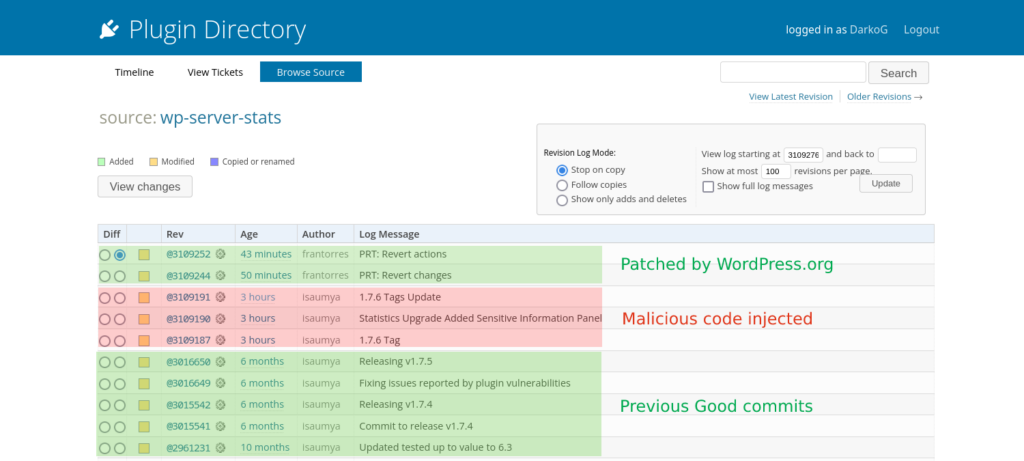
Finally the WP.org team is tagging patched version on behalf the author.
Prevention Measures
1. Take control of the plugin updates
To prevent your plugins to auto-update malicious version, you need to disable plugin updates for now.
At this point, do not trust the plugin repository and disable auto-updates temporarily by adding the following filter in your website code (specifically in mu-plugins or theme’s functions.php):
add_filter( 'auto_update_plugin', '__return_false' );2. Install updates manually
To ensure the plugins that you want to update aren’t infected, download the plugin and check the development log on WordPress plugin page or scan it with Virustotal.com and only after that upload the plugin to your site.
If you spot any issues or found infected plugin, report it to [email protected].
3. Backup your WordPress install regularly
Regularly back up your sites to ensure you can restore them in case a plugin gets infected through auto-update.